Once the ePassport chip has been accessed, ePassport validation can begin. At a minimum, this will involve a process called passive authentication. Passive authentication is the process of authenticating the digital signature to confirm that the information stored on the chip was saved by the proper authority (i.e. the issuing State) and has not been tampered with. According to ICAO Doc 9303, ePassport chips must contain a digital signature (which requires passive authentication to authenticate).
An issuing State may also choose to implement additional security mechanisms on the chip to protect against substitution (i.e. cloning)—active authentication, chip authentication, and/or PACE with Chip Authentication Mapping. If these mechanisms are available, the inspection system may also perform these functions. For information on these optional mechanisms, see Doc 9303, Part 11, Section 6.
When an ePassport is read by an inspection system at border control for the purpose of ePassport validation, there are multiple checks that are undertaken; therefore, the results should be interpreted by an application on the inspection system and provide the border officer with a simple response.
How these results are interpreted and displayed for a border officer and the operational procedures that should be followed for each would be determined by the Receiving State. No two States will have the exact same requirements and procedures. Section 3b provides more information on the considerations that should be taken into account when developing business requirements for the inspection system.
The inspection system should be able to display at least three potential responses:
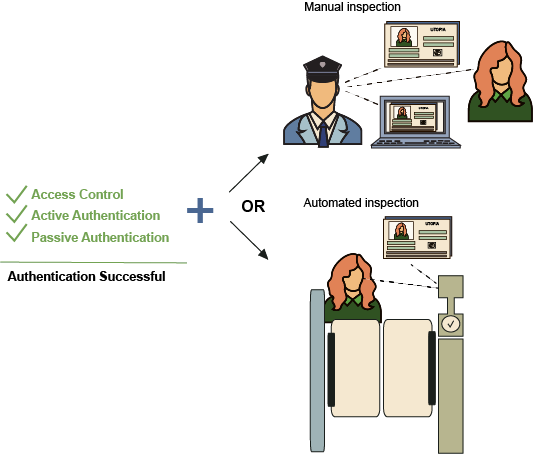
1-Authentication Successful
This result should be displayed when all verifications linked to the “e” part of the presented ePassport were successful. Passive authentication has confirmed that the data stored on the chip is genuine and has not been tampered with, and if supported by the chip, another process has confirmed that the chip is not a clone. To complete the authentication, the data displayed on the screen of the inspection system (i.e. populated from the data stored on the chip) should be compared against the physical document. This comparison can be conducted manually by a border officer or by an automated system.
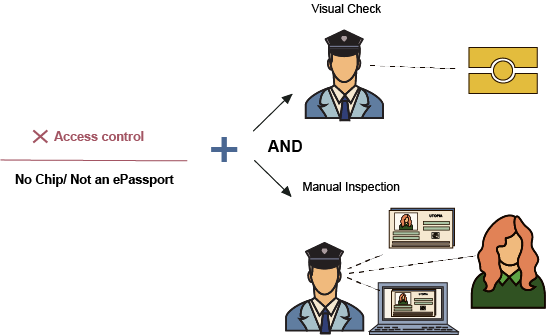
2-Authentication Failed: No chip/Not an ePassport
This result should be displayed when the passport is not responding to the reader. This can be caused by the provided passport being a non-electronic passport or if the ePassport has an electrical issue of some kind that does not allow it to communicate with the inspection system/reader. In this instance, the border officer should be instructed to verify if the document should be an ePassport (i.e. does the document have the “chip inside” symbol or is it from a State that only has ePassports in circulation?). If that is the case, then the officer may want to take a closer look at the document to ascertain whether it might have been tampered with to harm the chip; and, if necessary, refer the traveler to secondary inspection. If, however, the document is not an ePassport and has no indication that it should be, the border officer can proceed with usual inspection procedures.
3-Authentication Failed
In the most simplified version, this result (Validation Failed) can be displayed to the primary inspection officer (or by the automated system) for any possible failure in the chip validation process. However, this could result in a high through-put to secondary inspection. Many States will likely define additional underlying parameters to deal with variations in the PKI certificates available and develop corresponding operational procedures.

